EC6108V9C
Board
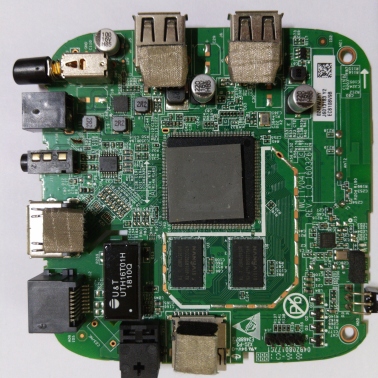

:USB_BOOT: J16 (near power switch)

bootargs
baudrate=115200
bootargs=console=ttyAMA0,115200 blkdevparts=mmcblk0:1M(fastboot),4M(bootargs),16M(recovery),1M(deviceinfo),4M(baseparam),4M(pqparam),4M(logo),16M(fastplay),8M(misc),24M(factory),12M(kernel),8M(iptv_data),340M(backup),340M(cache),520M(system),-(userdata)
bootargs_1G=mem=1G mmz=ddr,0,0,400M
bootargs_2G=mem=2G mmz=ddr,0,0,600M
bootargs_512M=mem=512M mmz=ddr,0,0,235M
bootcmd=mmc read 0 0x1FFBFC0 0x4B000 0x5000; bootm 0x1FFBFC0
bootdelay=0
bootfile="uImage"
gmac_debug=0
ipaddr=192.168.1.10
netmask=255.255.255.0
phy_addr=2,1
phy_intf=mii,rgmii
serverip=192.168.1.1
stderr=serial
stdin=serial
stdout=serial
use_mdio=0,1
verify=n
Flash layout
Name |
Offset |
Size |
Description |
|---|---|---|---|
fastboot |
0M |
1M |
|
bootargs |
1M |
4M |
U-Boot env file, sector size: |
recovery |
5M |
16M |
Android bootimg |
deviceinfo |
21M |
1M |
Model type, Serial No, MAC address, etc |
baseparam |
22M |
4M |
|
pqparam |
26M |
4M |
Video Post Processing parameters |
logo |
30M |
4M |
|
fastplay |
34M |
16M |
Fastboot DRM parameters (optional) |
misc |
50M |
8M |
empty |
factory |
58M |
24M |
empty |
kernel |
82M |
12M |
Android bootimg |
iptv_data |
94M |
8M |
|
backup |
102M |
340M |
ext3/4, Android A single |
cache |
442M |
340M |
ext3/4, Android |
system |
782M |
520M |
ext3/4, Android |
userdata |
1302M |
ext3/4, Android |
Fastboot
fastboot# getinfo ddrfree
DDR free region baseaddr:0x1000000 size:0x3F000000
fastboot# help
? - alias for 'help'
CXSecSystemBoot- Conax CA security system booting
base - print or set address offset
bootimg - boot application boot.img(kernel+ramdisk) from memory
bootm - boot application image from memory
bootp - boot image via network using BOOTP/TFTP protocol
ca_auth - verify android system: bootargs, recovory, kernel, system...
ca_cbcmac_test-
ca_common_verify_bootargs- ca_common_verify_bootargs
ca_common_verify_bootargs_partition- ca_common_verify_bootargs_partition
ca_common_verify_encryptimage- Encrypt image for Digital Signature
ca_common_verify_image_signature- verify pariton-image signature with tail mode
ca_common_verify_signature_check- verify BootArgs signature_check
ca_common_verify_system_signature- verify pariton-image signature with tail mode
ca_decryptflashpartition- decrypt flash_patition_name to DDR
ca_enablesecboot- ca_enablesecboot flash_type(spi|nand|sd|emmc)
ca_encryptboot- CA Encrypt Boot
ca_get_extern_rsa_key- get external rsa key
ca_getotprsakey- ca_getotprsakey
ca_getrsakeylockflag- ca_getrsakeylockflag
ca_getsecbootstatus- ca_getsecbootstatus
ca_lockrsakey- ca_lockrsakey
ca_setotprsakey- ca_setotprsakey
ca_special_burnflashname- Encrypt DDR image with R2R Key-ladder and burn DDR image into flash
ca_special_burnflashnamebylen- Encrypt DDR image with R2R Key-ladder and burn DDR image into flash
ca_special_verify- ca_special_verify flash_patition_name
ca_special_verifyaddr- ca_special_verifyaddr flash_patition_Addr
ca_special_verifybootargs- verify bootargs
cipher_cbc_mac_test-
clear_bootf- clear Hibernate!! bootflag
cmp - memory compare
cp - memory copy
crc32 - checksum calculation
ddr - ddr training function
fatinfo - print information about filesystem
fatload - load binary file from a dos filesystem
fatls - list files in a directory (default /)
getinfo - print hardware information
go - start application at address 'addr'
hash - Calcluate hash
hash_test- hash_test [x]:[0] SHA1; [1] SHA256; [2] HMAC-SHA1; [3] HMAC-SHA256;
help - print command description/usage
hibernate- Hibernate!! boot
loadb - load binary file over serial line (kermit mode)
loady - load binary file over serial line (ymodem mode)
loop - infinite loop on address range
md - memory display
mii - MII utility commands
mm - memory modify (auto-incrementing address)
mmc - MMC sub system
mmcinfo - mmcinfo <dev num>-- display MMC info
mtest - simple RAM read/write test
mw - memory write (fill)
nand - NAND sub-system
nboot - boot from NAND device
nm - memory modify (constant address)
otp_burntoecurechipset- Burn to secure chipset, please be careful !!!
otp_getchipid- otp_getchipid
otp_getcustomerkey- otp_getcustomerkey
otp_getmsid- otp_getmsid
otp_getsecurebooten- otp_getsecurebooten
otp_getstbprivdata- otp_getstbprivdata
otp_getstbsn- otp_getstbsn
otp_setstbprivdata- StbPrivData
otpreadall- read otp ,for example otpreadall
otpwrite- write otp ,for example otpwrite adddress value
ping - send ICMP ECHO_REQUEST to network host
printenv- print environment variables
rarpboot- boot image via network using RARP/TFTP protocol
reset - Perform RESET of the CPU
saveenv - save environment variables to persistent storage
setenv - set environment variables
setproflag- --- setflags to product test page
tftp - tftp - download or upload image via network using TFTP protocol
unzip - unzip a memory region
uploadx - upload binary file over serial line (xmodem mode)
usb - USB sub-system
usbboot - boot from USB device
version - print monitor version
Boot log
Bootrom start
Boot from eMMC
Initializing DDR ... OK
Starting DDR training ... OK
Starting fastboot ...
System startup
Reg Version: v1.1.0
Reg Time: 2016/2/25 9:23:54
Reg Name: hi3798mdmo1g_hi3798mv100_ddr3_1gbyte_16bitx2_4layers_emmc.reg
Relocate Boot to DDR
Jump to DDR
Compressed-boot v1.0.0
Uncompress.......................Ok
System startup
Reg Version: v1.1.0
Reg Time: 2016/2/25 9:23:54
Reg Name: hi3798mdmo1g_hi3798mv100_ddr3_1gbyte_16bitx2_4layers_emmc.reg
Relocate Boot to DDR
Jump to DDR
Fastboot 3.3.0-00709-ga3bdc60-dirty (liuhh@HW-TV-S5) (Jul 07 2016 - 12:33:43)
Fastboot: Version 3.3.0
Build Date: Jul 7 2016, 12:34:51
CPU: Hi3798Mv100 (CA)
Boot Media: eMMC
DDR Size: 1GB
Check nand flash controller v610. found
Special NAND id table Version 1.36
Nand ID: 0x00 0x00 0x00 0x00 0x00 0x00 0x00 0x00
No NAND device found!!!
MMC/SD controller initialization.
MMC/SD Card:
MID: 0x11
Read Block: 512 Bytes
Write Block: 512 Bytes
Chip Size: 7456M Bytes (High Capacity)
Name: "008G3"
Chip Type: MMC
Version: 4.0
Speed: 52000000Hz
Bus Width: 8bit
Boot Addr: 0 Bytes
Boot Env on eMMC
Env Offset: 0x00100000
Env Size: 0x00010000
Env Range: 0x00010000
HI_OTP_LockIdWord,327: ID_WORD have already been locked
SDK Version: HiSTBAndroidV600R001C00SPC063_v2016022921
=====FILE: higo/adp_gfx.c, LINE: 150, Ret:b0038002
=====FILE: higo/adp_gfx.c, LINE: 194, Ret:b0038002
=====FILE: higo/adp_gfx.c, LINE: 388, Ret:b0038002
=====FILE: higo/hi_go_bliter.c, LINE: 149, Ret:b0038002
Security Begin Read RSA Key!
Secure boot is enabled
get key value 0x0
HI_Flash_Read Ret= 3072
HI_Flash_Read Ret= 3072
HI_Flash_Read Ret= 10485760
HI_Flash_Read Ret= 10485760
******** boot from kernel...********
[HMT]Verify kernel begin.
HI_Flash_Read Ret= 1024
HI_Flash_Read Ret= 1024
The kernel size is [0]
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
[HMT] RSA Verify the kernel Error.
[HMT] Check RSA ERROR!!
[HMT] The kernel verify failed.
HI_Flash_Read Ret= 512
HI_Flash_Read Ret= 512
Stb mac is : [XX:XX:XX:XX:XX:XX]
hpm_code_average = 0x106
Reserve Memory
Start Addr: 0x3FFFE000
Bound Addr: 0x8E64000
Free Addr: 0x3F73C000
Alloc Block: Addr Size
0x3FBFD000 4194304
0x3F8FC000 3145728
0x3F87B000 524288
0x3F878000 8192
0x3F843000 212992
0x3F742000 1048576
0x3F73E000 12288
0x3F73D000 0
0x3F73C000 0
Press Ctrl+C to stop autoboot
kernel @ 3e08000 (2572288 bytes)
ramdisk @ 4e00000 (2347778 bytes)
page size @ 2048 bytes
initrd rd_start = 4e00000,rd_end = 503d302
## Booting kernel from Legacy Image at 01ffc7c0 ...
Image Name: Linux-3.10.0_s40
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 2572224 Bytes = 2.5 MiB
Load Address: 02000000
Entry Point: 02000000
load:2000000,blob_start:1ffc7c0,blob_end:22707c0,image_start:1ffc800,image_len:273fc0
Loading Kernel Image ... OK
OK
kernel loaded at 0x02000000, end = 0x02273fc0
images.os.start = 0x1FFC7C0, images.os.end = 0x22707c0
images.os.load = 0x2000000, load_end = 0x2273fc0
ret -2
initrd rd_start = 4e00000,rd_end = 503d302
Starting kernel ...